Neat Info About How To Detect Conficker Virus
Conficker, as of this writing, is nearly eight years old, and almost every antivirus available today can detect and quarantine the worm before it spreads.
How to detect conficker virus. Ad best antivirus software review 2022. If you choose not to. Choose from a wide range of antivirus & device security solutions.
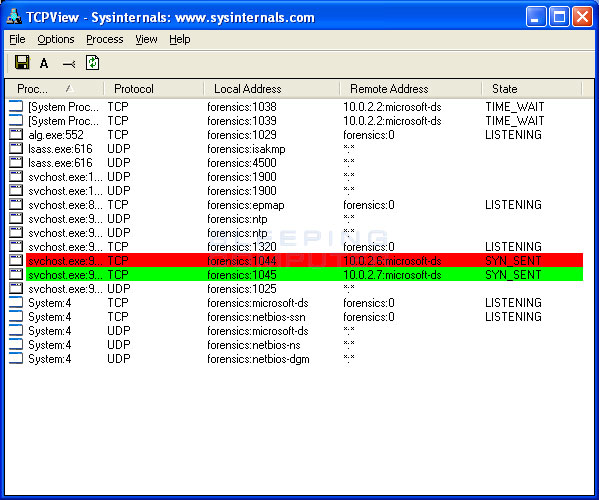
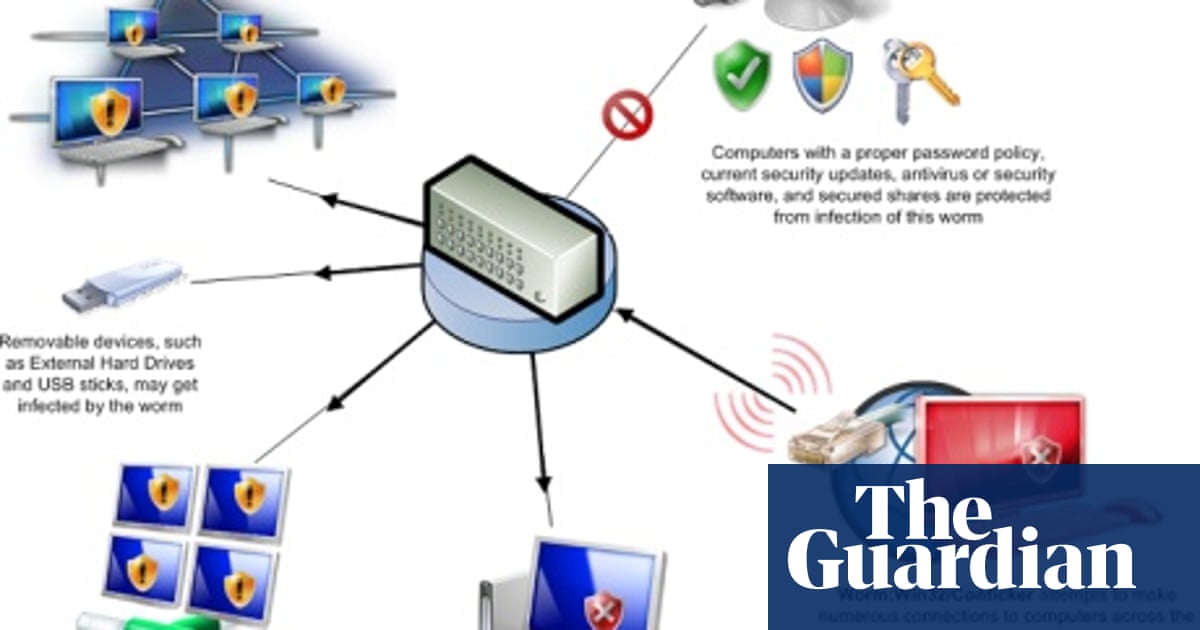
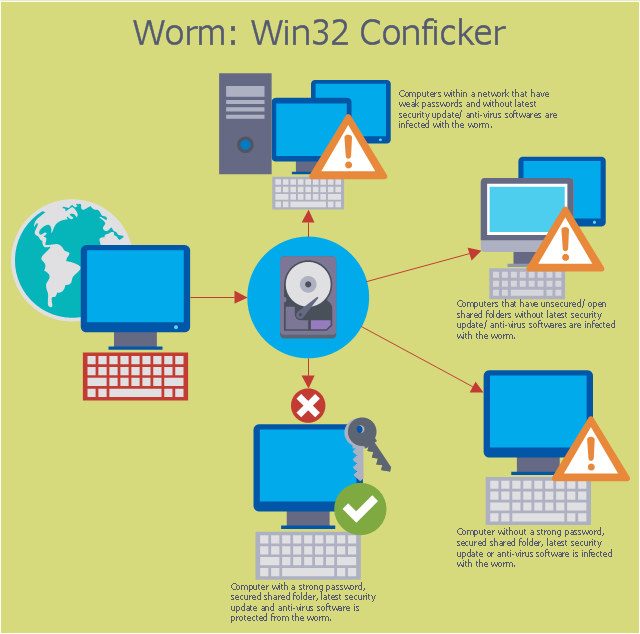
Monitor the security event log on your domain controller (s) for event ids of 529 (if no 529 events are occurring, then win32/conficker is using correct administrative. Account lockout policies being reset automatically. Even though more than 15 million ( some are saying more than 20 million) computers are infected, they are still saying it's not that bad, but trust me.
Choose your antivirus protection today. Change your passwords, and make them strong. Ad protect your devices from cyber attacks, malware, identity theft & identity theft.
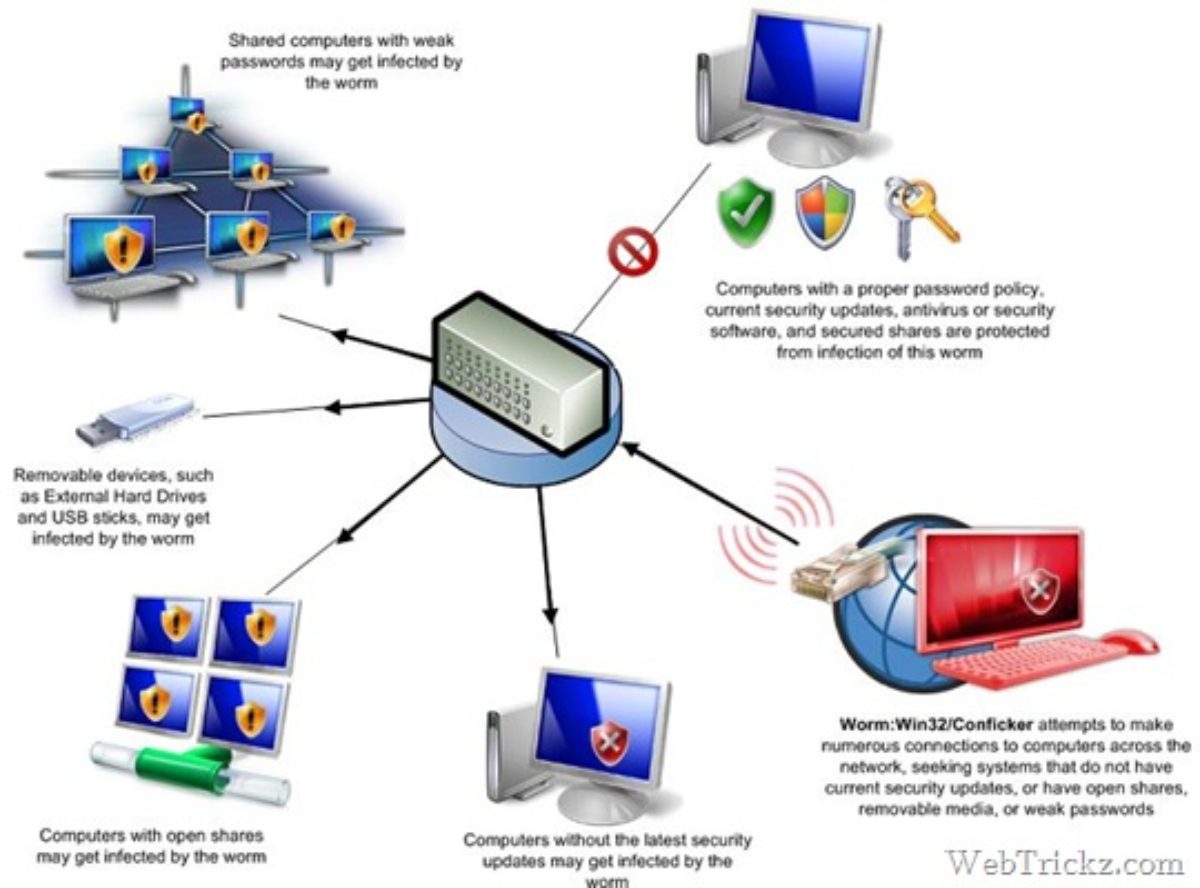
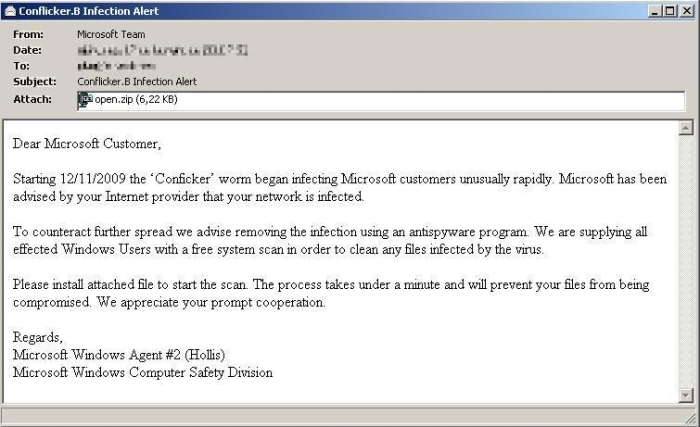
Please download malwarebytes to your desktop. Symptoms of a conficker infection include: Protect your computer from viruses & malware.
Ad guardio antivirus scan & protects chrome from viruses, phishing, malware & other threats. Fast, free antivirus software 2022. The presence of an infection may be detected if users are.
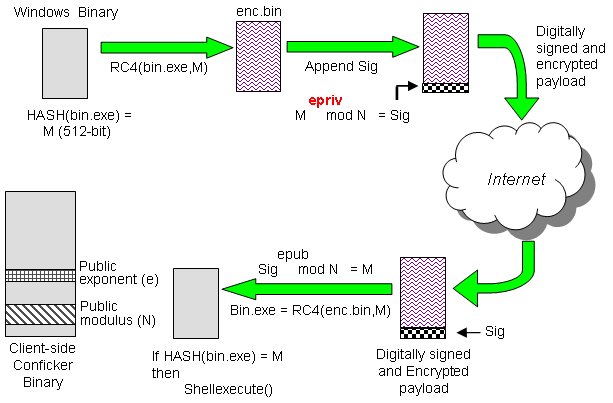
The conficker virus uses a vulnerability in older windows operating systems netbios to install itself as a dll file with registry keys to run as an invisible program in the background. The latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139 and port 445. We create a secure digital world for over 1m users around the world.